Reinventy Shield™ V2
Tactical Edge Super‑Node (Non‑Wearable Edition) - A portable, air‑gapped micro‑datacenter for mission planning, CI/CD, classified data custody, and swarm control.
Shield V2 condenses a ground station, a DevSecOps factory, a secrets vault, and a threat‑aware network gateway into a single, fan‑less unit. It runs entirely on open, audit‑ready software and NVIDIA Jetson edge compute, allowing you to plan, authorize, and launch autonomous missions from a secure desk‑edge node with no cloud dependency. The non‑wearable edition is built for labs, command rooms, and mobile command posts that require silent operation, low power, and full data sovereignty.
Outcomes: faster time‑to‑mission, verifiable chain‑of‑custody, selective RF exposure (burst‑only), and on‑prem control of UAV swarms—without vendor lock‑in.
What’s New in V2
Mission I/O Core: MAVProxy bridge (Serial↔UDP) as the single authority over flight‑controller serial, eliminating port contention and latency drift.
Live Telemetry Fabric: UDP collectors feeding Redis + REST/WebSocket dashboard (“droneweb”) for real‑time fleet status and health.
Autostart & Recovery: All services containerized with
restart: unless-stopped; cold‑start to operational link in under 90 s.EMCON‑Aware Connectivity: Burst‑on LTE/5G or Starlink Direct‑to‑Cell, MANET mesh fallback, Iridium keep‑alive; RF duty‑cycle engineered for < 1 % in stealth profiles.
DevSecOps Offline: Gitea + Drone CI/CD pipeline to build, sign, and deploy mission containers inside the air‑gap; Cosign‑signed artifacts.
Vault‑Grade Security: HashiCorp Vault for KMS and one‑shot keys, Vaultwarden for operator credentials, Suricata + TheHive/Cortex for NIDS and automated response.
Deploy‑Attach Mode: One‑gesture mission ingest → verify → authorize → propagate to the swarm, then automatic RF mute.
Form‑Factor Updates: Silent desk‑edge enclosure, EMI‑tight, optional TPM 2.0 + tamper‑erase. Same software stack as the wearable, tuned for fixed‑site duty.
V2 at a Glance (Non‑Wearable Edition)
Role: On‑prem mission server, secure swarm controller, private Git/CI/CD, secrets vault, and VPN/proxy bastion.
Compute: NVIDIA® Jetson (Orin NX 16 GB recommended) delivering ≈ 157 TOPS INT8 for on‑edge AI (vision, SLAM, event filters, µLLM ops‑chat).
Network: Dual GbE (MACsec‑ready), Wi‑Fi 6E, optional LTE/5G modem, Starlink D2C blade, MANET radio via USB 3.2, Iridium fallback.
Power/Noise: 15–25 W typical, fan‑less, lab‑safe acoustics.
Software: 100 % FOSS/COTS containers; MOSA/SOSA aligned; zero vendor telemetry.
Why the Non‑Wearable Edition Exists
Some missions never leave the building—black‑program R&D, red‑team ranges, strike planning, or forensic labs. The V2 non‑wearable node gives you a sealed, zero‑trust micro‑cluster that stays inside your perimeter yet retains the exact same mission logic as the field system: deploy‑attach, selective RF, swarm orchestration, and full DevSecOps offline. You control the stack end‑to‑end and keep every byte on premises.
Core Capabilities (Technical + Commercial Value)
Plan & Authorize: Ingest signed mission packages, enforce BioPrint™/PIN/geo‑fence/time‑fence, and produce verifiable audit logs.
Value: provable compliance, reduced legal risk, faster approvals.Build & Deploy in an Air‑Gap: Gitea + Drone CI/CD sign and push containers to drones without touching external networks.
Value: cuts cloud costs, eliminates vendor lock‑in, speeds iteration.Swarm Control & Telemetry: MAVProxy governs all serial; UDP telemetry fans out to dashboards and analytics; supports 10–60 UAVs per burst window (scenario‑dependent).
Value: scales from pilot trials to squadron‑level ops with the same node.Selective Connectivity (EMCON): LTE/5G and Starlink D2C open for 2–5 s bursts, then auto‑mute; MANET mesh and Iridium for contested links.
Value: low intercept probability, minimal triangulation risk.Secure Network Gateway: WireGuard + Headscale in concentrator mode, hardened Nginx reverse‑proxy/WAF, full‑tunnel DNS‑over‑TLS, threat‑aware auto‑shutdown.
Value: stands up a cloaked enclave in minutes; acts as the cryptographic heart of the mission LAN.Data Sovereignty & Wipe: Vault‑managed one‑shot keys, TPM‑sealed secrets, tamper‑erase in < 150 ms, immutable time‑stamped logs.
Value: classified‑grade custody without buying proprietary appliances.
Typical Non‑Wearable Scenarios
Mission Planning Cell: Build, sign, and stage mission bundles; run pre‑strike checks; schedule deploy‑attach windows.
Lab & R&D: Prototype AI pipelines on Orin NX; test swarm behaviors; simulate RF‑burst policies without internet.
Secure Proxy Bastion: Front Git/Vault/NIDS behind mutual‑TLS; micro‑segment field tablets and analyst workstations via WireGuard.
Mobile Command Post: Silent node in a vehicle rack or table mount; same CI/CD and RF‑burst controls used in the field.
Headline Metrics (Nominal Targets)
Cold‑start → operational link: < 90 s
Swarm provisioning in one burst: 10–60 UAVs (payload size dependent)
RF burst window: 2–5 s, duty‑cycle < 1 % in stealth mode
Uplink per drone (event‑driven ROI): 8–20 kbps typical
Telemetry fan‑out: sub‑100 ms to dashboard over LAN
For engineering and procurement: Shield V2 replaces a stack of servers, a ground station, a VPN concentrator, and a secrets appliance with one open, auditable node. For operations: it shortens launch timelines and lowers your RF footprint. For finance: it delivers prime‑contractor capability without prime‑contractor lock‑in..

Deploy‑Attach™ Mission Loading
One‑gesture mission ingest, verify, authorize, propagate.
Description
Shield receives a signed mission package, verifies it with a multi‑factor policy (BioPrint™, PIN, geo/time‑fence), authorizes it, and pushes it to the swarm within a single RF window. Radios then shut down. Everything stays air‑gapped with immutable logs.
Technical Specification
Ingest: signed bundles + integrity attestation.
Policy: BioPrint™ + PIN + geo/time‑fence.
Propagation: payload segmentation and per‑drone one‑shot keys.
Nominal timing: 15–30 s end‑to‑end; cold‑start → link < 90 s.
Audit: time‑stamp + Merkle proof stored in Vault.
Key Applications
Strike planning with controlled approvals.
Autonomous ISR launch in contested areas.
Mission re‑tasking via scheduled bursts.

EMCON & Anti‑Jam Suite
Open → Close → Vanish. Communications only when needed.
Description
LTE/5G or Direct‑to‑Cell satellite links open for 2–5 s, transfer data, then shut down. Low‑power MANET as fallback. Iridium for keep‑alive. RF duty‑cycle < 1%. On‑drone ECCM algorithms on Jetson reduce jamming effectiveness; the swarm remains operational even under full radio blackout.
Technical Specification
Burst control: schedulable RF windows, auto‑mute.
Links: LTE/5G, Starlink D2C, MANET, Iridium.
ECCM on‑drone: adaptive FHSS, DSSS, jammer detection, null‑steering (with compatible antennas), autonomy fallback.
Encryption: AES‑GCM one‑time keys per burst.
Conditional re‑open: pre‑strike imagery, sensor thresholds, abort/RTB.
Key Applications
Low‑signature RF operations.
Penetration in aggressive EW environments.
Beyond‑line‑of‑sight swarm coordination.

BioPrint™ Dual Biometric + Biochemical Sensor
Identity and physiological state in one gesture.
Description
Hybrid sensor: high‑resolution fingerprint + bio‑impedance spectroscopy of sebaceous secretions using nickel filaments on a Clear V4 substrate. Reduces spoofing, binds authorizations to the real operator, enables safety‑grade physiological checks.
Technical Specification
Fingerprint: 5 µm CMOS + on‑edge CNN.
Bio‑impedance: Ni filaments 0.025 mm, 12‑bit ADC, 8 channels.
Interfaces: SPI/I²C to Jetson; encrypted sample transport.
Policy: combined, time‑boxed unlock; non‑persistent data in RAM.
Key Applications
Authorization for missions and critical actions.
Custody of classified data on‑prem.
Operator traceability in chain‑of‑custody.

Swarm Orchestration Engine
Provisioning and control up to squad level.
Description
Fleet management with leader–follower, sector partitioning, and route de‑confliction. Provisioning of 10–60 UAVs per burst (payload‑dependent). Event‑compressed telemetry; conditional re‑open rules. Fully attested and repeatable.
Technical Specification
3‑D planner; per‑drone waypoint stacks.
Edge‑optimized RL for de‑confliction (SWaP profiles).
Telemetry on LAN < 100 ms; typical uplink per drone 8–20 kbps.
Compatibility with modular MAVLink‑like controllers and payloads.
Key Applications
Multi‑sensor ISR.
Target saturation with stealth drones.
Cooperative area reconnaissance.

Edge AI Compute (Jetson Orin NX 16 GB)
157 TOPS in a fanless desk node.
Description
Vision, SLAM/VIO, event filters, and µLLM decision support run locally. No cloud. The operator can simulate, validate, and push mission containers while remaining air‑gapped.
Technical Specification
Compute: ≈ 157 TOPS (INT8); 50 TOPS FP16; 7 TFLOPS FP32.
CPU: 8× Arm Cortex‑A78AE @ 2 GHz; LPDDR5 16 GB @ ~102 GB/s.
Power: 15–25 W typical; fanless.
Pipeline: local build‑sign‑deploy of containers.
Key Applications
Target and scene recognition.
SLAM in GNSS‑denied scenarios.
On‑prem textual assistance to operators.

Secure Network Gateway
VPN hub, reverse‑proxy/WAF, zero‑trust enclave.
Description
The node acts as a WireGuard concentrator, mTLS reverse‑proxy bastion, and full‑tunnel egress with DNS‑over‑TLS. If hostile probing is detected, services vanish and reappear only after an authorized knock.
Technical Specification
Mesh VPN with micro‑segmentation.
Single mTLS front‑end on 443; strict HSTS and CSP.
Auto‑shutdown on IOCs; pattern‑based re‑open.
Immutable logging in Vault.
Key Applications
Encrypted bubble for planning cells.
In‑house bastion for Git/Vault/NIDS.
Remote ops over untrusted networks.

Triple‑Layer Armor & HXT Stealth Skin
EMI‑tight, fire‑barrier, HXT composites for reduced signature.
Description
Three‑layer shell: EMI liner in Formlabs ESD Resin, thermal barrier in High‑Temp Resin, and outer shell in Nylon‑12 CF reinforced with Kevlar. Proprietary HXT finish attenuates RF/IR reflections and vibrations. IP‑67, no fans, no vents.
Technical Specification
EMI: charge dissipation, local RF attenuation.
Fire barrier: HDT > 238 °C; thermal containment.
Armor: carbon‑filled + Kevlar; vibration damping.
Weight: < 800 g (typical configs).
Key Applications
Classified labs; mobile command rooms.
Posts in electromagnetically noisy environments.
Continuous transport and use in harsh conditions.
Radar/Signal Awareness & Threat Intel
From RF noise to operational risk in seconds.
Description
Passive ingest of radar/ADS‑B/MLAT tracks and ELINT/MANET feeds; correlation with swarm telemetry and EMCON policy. Real‑time alerts and automated defenses (drop listeners, rotate keys, RF blackout).
Technical Specification
Parsers for standard feeds; event normalization.
Correlation with swarm positions and AOIs.
Automated responders tied to IOCs and thresholds.
Cases and logs handled in the internal analytics platform.
Key Applications
Pre‑strike sanity check on threats.
De‑risking routes and timing for ingress/egress.
Immediate countermeasures to hostile probing.

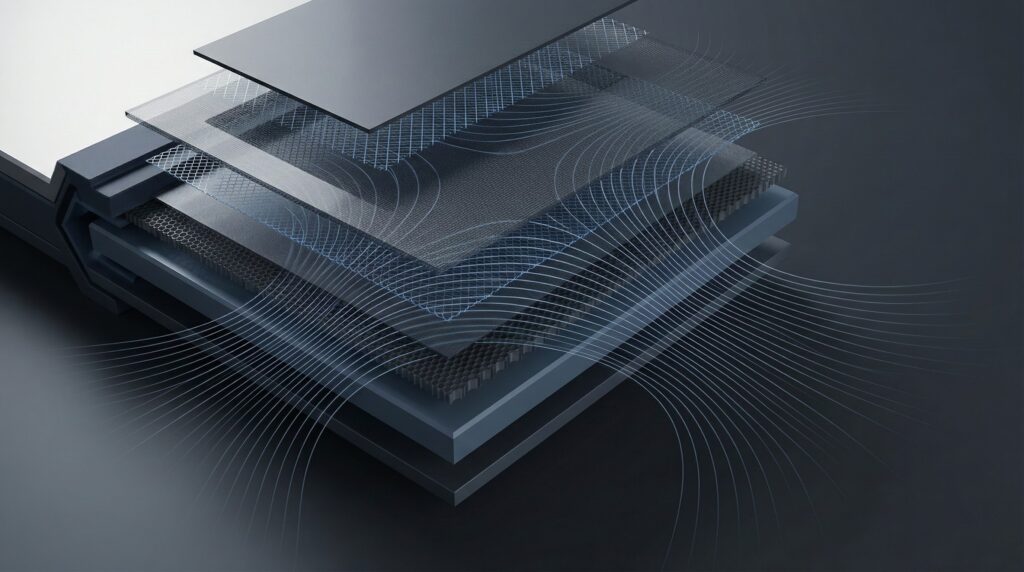
In‑House Full Mode (Non‑Wearable)
A classified server room the size of a book.
Description
The same mission logic as the wearable, in a desktop form. Offline DevSecOps, secrets vault, NIDS, local AI inference. Radios off by default for TEMPEST policies; can be enabled inside shielded cages.
Technical Specification
Encrypted NVMe; nightly snapshots.
mTLS LAN access; optional full‑tunnel for remote clients.
Typical simultaneous users: 10–20 (R&D profile).
Continuous power ~15 W; zero acoustics.
Key Applications
Strike/ISR planning cells.
Black‑program R&D.
Bastion for ad‑hoc remote teams.
Materials & Sustainability
A classified server room the size of a book.
Description
Materials and processes are chosen for robustness and sustainability: industrial 3‑D printing, COTS components, easy part replacement, transparent supply chain. No lock‑in, full auditability.
Technical Specification
3‑D‑printed shell and inserts; swappable parts.
COTS BOM; modular radio components.
Recyclability and field repairability.
Key Applications
Fleet upkeep in theater.
Rapid versioning for government customers.
Simplified audit and procurement.
• Reinventy Solutions is not responsible for comments, interpretations or re‑use made by third parties.
• All specifications are preliminary and may change without notice; shared links should therefore cite the original URL.
• This limited permission does not convey any licence to our trademarks, images or technical data beyond the context of the original page.
See the full Master Technology & Commercial Disclaimer .


